How Is Cloud Technology Used To Secure Data?

According to some estimates, there is one cyberattack every 39 seconds. This might not sound like a lot, but it increases daily, and there is no indication that this number will ever fall. Moreover, if you happen to be that one person who is hacked and has your sensitive data stolen, all you will care about is how it occurred and why you didn't take additional steps to keep your information safe. There are various ways to keep your information secure, but the most prominent and manageable option is storing it in the cloud. This article will discuss how and why cloud storage is the safest way to protect your data.
Cloud Technology Provides Secure Data Storage By Distributing Data Across Different Servers And Locations
By distributing the data across different servers and locations, cloud technology ensures that no single server can hold all the sensitive data needed to access it. This way, if one of the servers becomes compromised, the rest of your data remains safe and secure, isolated from the affected areas of the server. You can read more about the benefits of spreading your data across multiple locations, but not only does it provide better security, but it can also reduce risk. Because numerous servers store parts of the whole dataset, a backup strategy is easier to implement since parts of the dataset will always be stored elsewhere. This also means maintaining availability is more accessible even if one server goes down or becomes unavailable for whatever reason. Generally speaking, distributing and storing your data via the cloud makes it more secure and more easily accessible. Be sure to do your research on the specifics of network setup, meaning of iops, and other factors to ensure your data gets the best possible treatment. Not all cloud providers are created equal, so it is essential to do your research before selecting one.
Authentication And Access Control Mechanisms Enable Granular Data Control
One of the most significant issues with physical storage is the threat of having to plug your device into someone else computer, leaving you vulnerable to whatever crazy Internet Explorer extensions they thought best to download and infect their computer with. Instead, the cloud allows you to share large files with ease, all the while keeping the rest of your data free from prying eyes. For example, if you happen to use Google Drive, you can create all kinds of data using Docs, Sheets, or whatever tools you might need. Once completed, you can share them with others in your team and choose to allow them to edit or view only, keeping your originals safe from unauthorized tampering and the rest of your data on the drive private. This can be particularly useful if you need to generate a collaborative document you will send to a client. You can disable the client from seeing the previous iterations and only allow them to view the final product. Some cloud providers will even allow you to add outside individuals to collaborate further while still keeping previous versions private. Moreover, working with a trusted corporate security partner can help ensure that strict authentication and access control mechanisms are in place to safeguard your data. Whether it's through multi-factor authentication or role-based access control, these measures ensure that only authorized individuals have access to your sensitive data.
It Ensures That Data In Transit And At Rest Cannot Be Intercepted Or Accessed By Unauthorized Parties
When data is in transit, usually when it's being sent or revived from a server, encryption technology scrambles it so that only the intended recipient can access it. This helps keep malicious actors from "listening in" and reducing the chances of a man-in-the-middle attack. At rest means simply how data sits on servers or other application environments waiting to be used, viewed, or transmitted. Cloud service providers often use various types of encryption technology to ensure no one can access the stored data without authentication and authorization. This ensures hackers are thwarted at the first hurdle by in-built security measures.
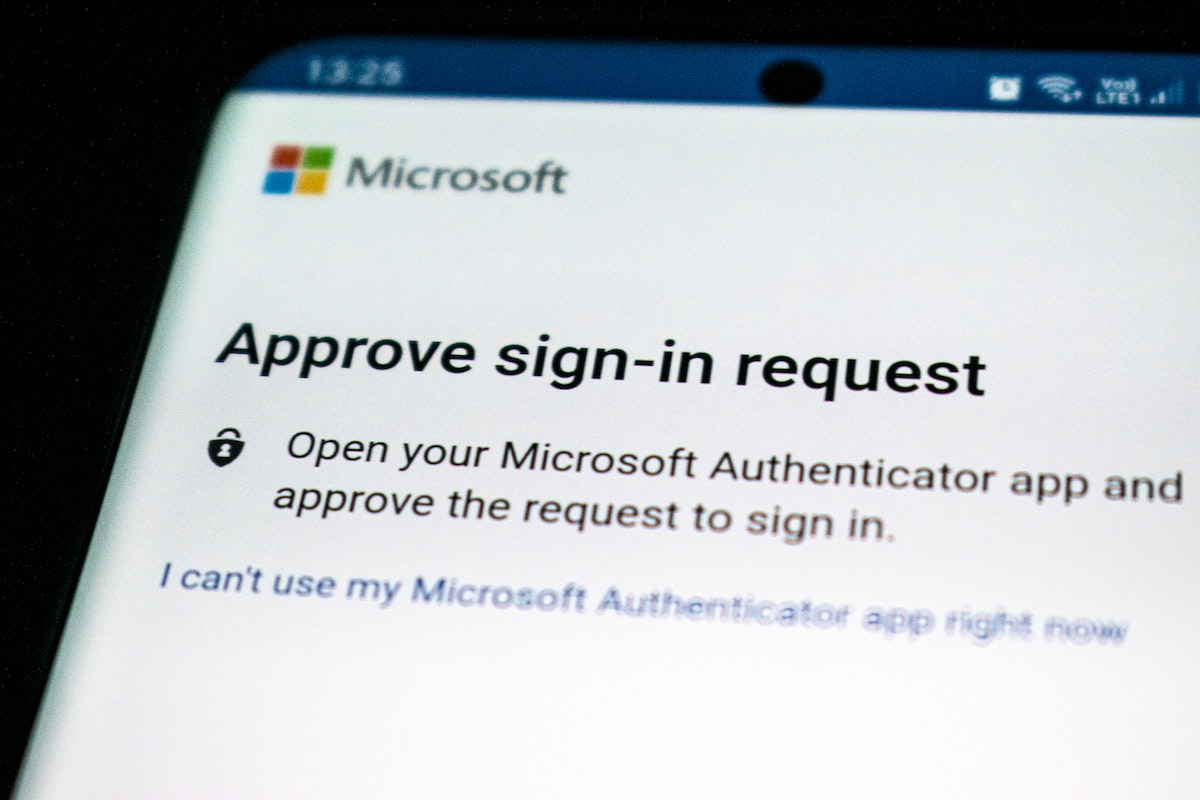
You Can Use Multi-Factor Authentication To Add An Extra Layer Of Security
Despite the fact that the fear hackers and other nefarious actors have created around your data, multifactor authentication (MFA) can create an almost impenetrable fortress around your data. By using MFA, you're adding another layer of security beyond just your username and password. Even if your credentials are compromised, hackers won't be able to access your account without the additional code. In many cases, this code will expire if it's not used within a specific time, further increasing your security. MFA can help protect both personal and corporate data stored on cloud servers by preventing unauthorized access while giving all users peace of mind their data remains secure.
Cloud Providers Automatically Apply Updates And Patches To Address Vulnerabilities
One of the most valuable aspects of utilizing cloud technology to secure your data, rather than doing it yourself, is that many of the better providers will update and harden their security measures to stay up to date with the latest threats. If you were to do this yourself, you would need to create a dedicated IT department and staff it with many very intelligent and expensive employees whose job is to monitor and patch your in-house systems. This is restrictive for most businesses, let alone individuals, but something that cloud providers offer as part of their service.
Cloud-based storage offers a myriad of benefits over storing data yourself. Aside from the security advantages, it's often more manageable to access and transfer data when stored on a hardened server within the vaults of a mega-corporation.
Updated July 24, 2023



